Cyber Security AI
Trust but Verify
Mitigating the Threats - Cybersecurity Best Practices - Regularly Update and Patch Software to Protect Against Vulnerabilities, Continuous Training& Verify Sources before taking action.

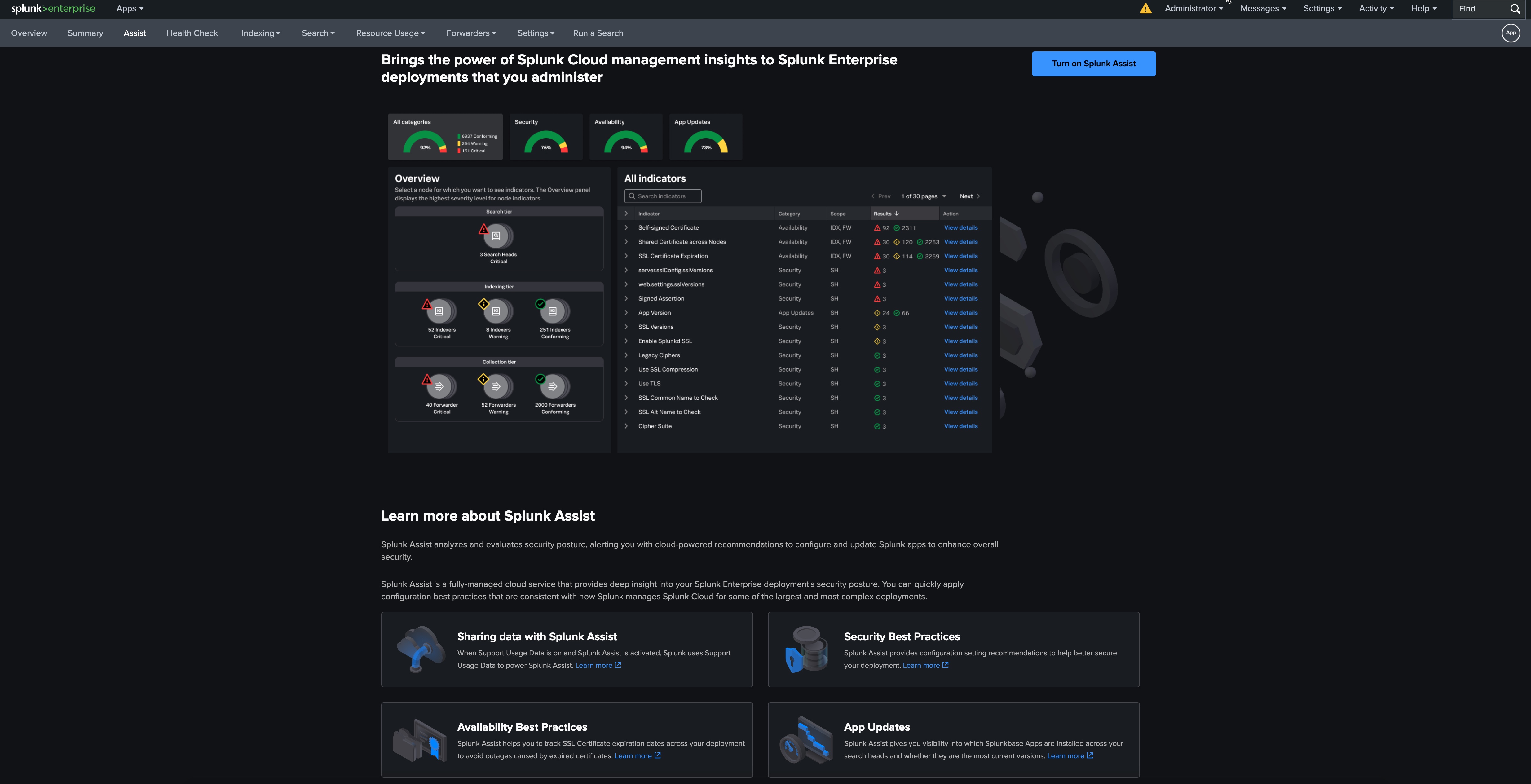
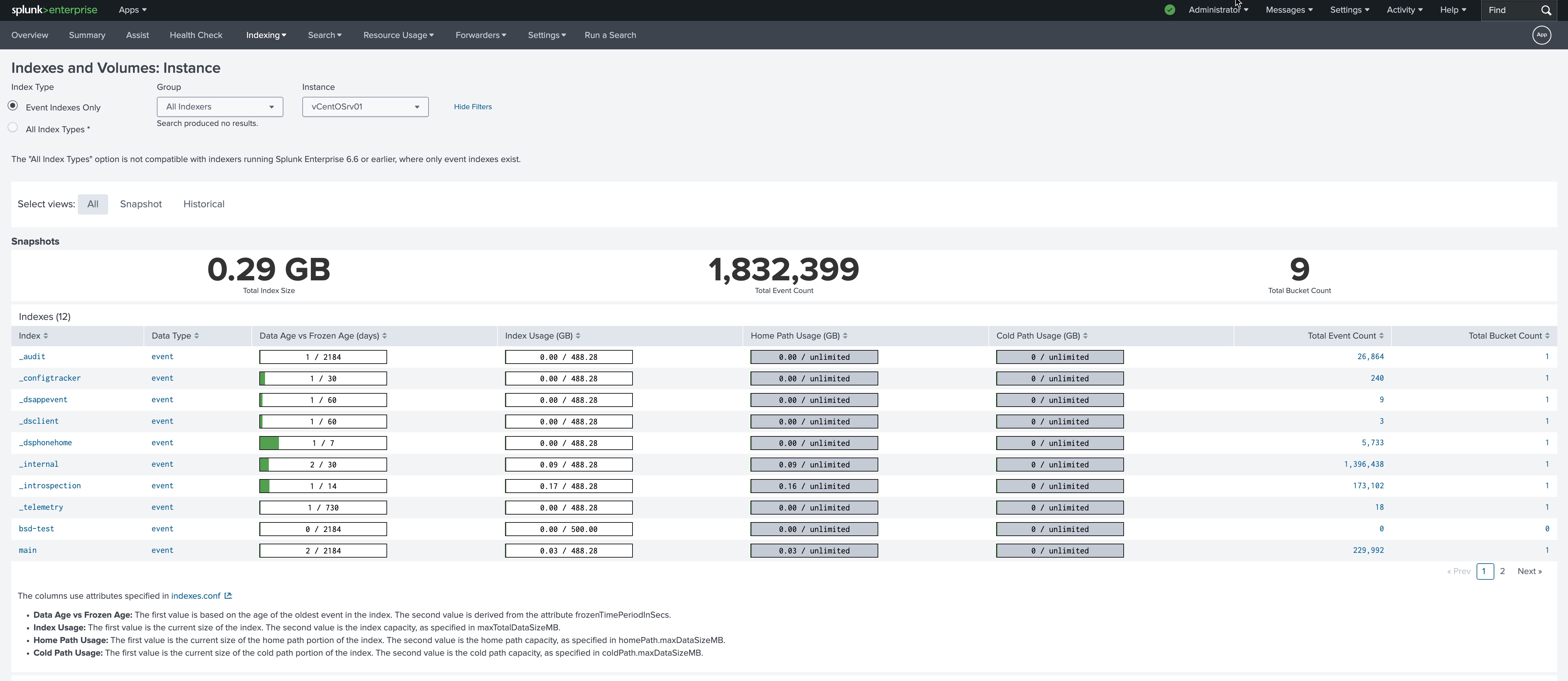
Splunk Enterprise v9.3.2 & Universal Forwarder 
Splunk is a big data platform that simplifies the task of collecting and managing massive volumes of machine-generated data and searching for information within it. The technology is used for business and web analytics, application management, compliance, and security https://www.splunk.com/en_us/products.html
"Real-time Visibility"
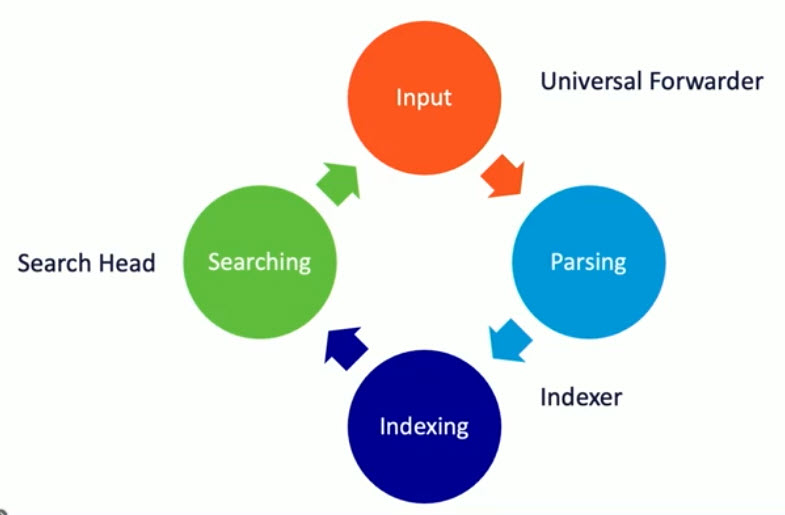
Automate the collection, indexing and alerting of machine data that's critical to your operations
"Data Source Agnostic"
Uncover the actionable insights from all your data no matter the source or format
"AI & Machine Leaning"
Leverage artificial intelligence and machine learning for predictive and proactive business decisions
I recommend checking the following resources:
- Splunk Documentation: The official Splunk documentation is the best source for detailed information about specific versions, including release notes, installation guides, and compatibility information.
- Splunk Releases: Check the Splunk website for official announcements and release notes for Splunk 9.3.2.
- Splunk Community: The Splunk community forums and other online resources can provide valuable insights and discussions related to specific Splunk versions.